ISO 27001
El Reto
La seguridad de la información es una responsabilidad de gobernanza corporativa. No puede ser vista como una iniciativa aislada del equipo de Tecnología de la Información, y sí como un tópico de estrategia de negocio. Dentro de esta perspectiva, las organizaciones han luchado para proteger informaciones controladas, críticas y/o confidenciales de accesos indebidos que pueden causarle daños irreversibles al negocio.
La familia de normas ISO 27000 ayuda a las organizaciones a mantener en seguridad sus activos de información. Adoptar esa familia de normas ayuda a las organizaciones a administrar la seguridad de los activos, tales como informaciones financieras, propiedad intelectual, detalles de los funcionarios o informaciones confiadas por terceros. La ISO/IEC 27001 es la norma más conocida de esa familia y contempla los requisitos para el sistema de gestión de seguridad de la información (SGSI).
ISO 27001 Solution
SoftExpert ofrece la solución de software más amplia y avanzada para la gestión de seguridad de la información, atendiendo las necesidades de los más rigurosos reglamentos globales. El SoftExpert Excellence Suite ayuda a las empresas a adherir a la norma ISO/IEC 27001, reduciendo los costos de conformidad, maximizando el éxito, aumentando la productividad y reduciendo los riesgos.
La solución de SoftExpert permite que las organizaciones atiendan los requisitos de la ISO/IEC 21001 de forma fácil, asegurando los tres pilares de seguridad de la información conocidos como la tríada CID (confidencialidad, integridad y disponibilidad). La misma ayuda en la gestión de riesgos, controles, políticas de seguridad de la información, activos, incidentes, proveedores, indicadores de desempeño, procesos, entre otros. Esto aumenta la eficiencia de la organización y reduce el retrabajo y el desperdicio.
Con recursos de colaboración en línea, la organización y sus gestores pueden comunicar y ser actualizados sobre las iniciativas de conformidad, involucrando a más usuarios, equipos, oficinas y unidades de negocio a través de un abordaje sistemático y unificado para obtener la excelencia em la gestión de seguridad de la información.
Screenshots
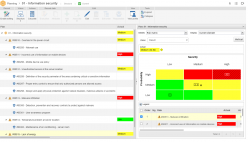
Evaluación de riesgos
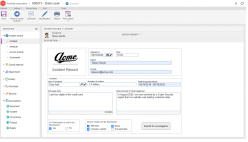
Gestión de incidentes
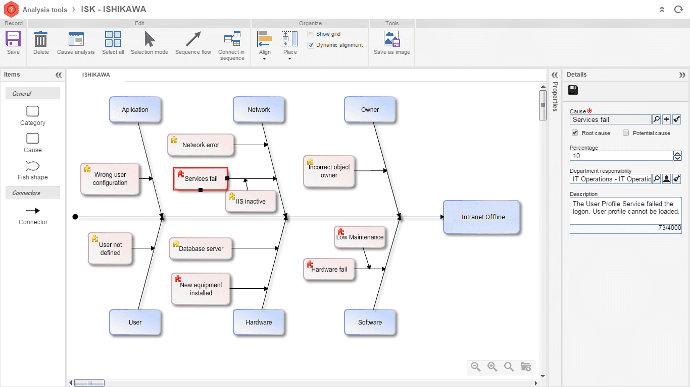
Gestión de problemas
Portal operacional
Principales Beneficios
Establish security requirements and objectives.
Usa un framework para identificación de los riesgos para la seguridad de la información y para la implementación de los debidos controles técnicos.
Garantiza conformidad con los tres pilares de seguridad de la información: confidencialidad, integridad y disponibilidad (CID).
Define los procesos que controlan y revisan la gestión de seguridad de la información.
Audita el grado de conformidad con políticas, directivas, normas y procedimientos.
Provee informaciones relevantes del sistema de gestión de la información a los proveedores y aliados de negocios.
Mejora la habilidad de recuperación en caso de falla y de mantenimiento de las actividades del negocio.
Reduce el costo con la reducción del número de incidentes.